New Protection Against Vote-Selling & Coercion
We are excited to share a new Zero Knowledge tool we've developed:
This new Overrides capability complements our existing bounty-based Vote Seller’s Dilemma. It is an optional extension for high stakes SIV elections to protect against vote-selling and coercion. This builds upon feedback from HACK SIV at DEF CON 2024, where vote-buying threats and coercion risks were a top raised concern.
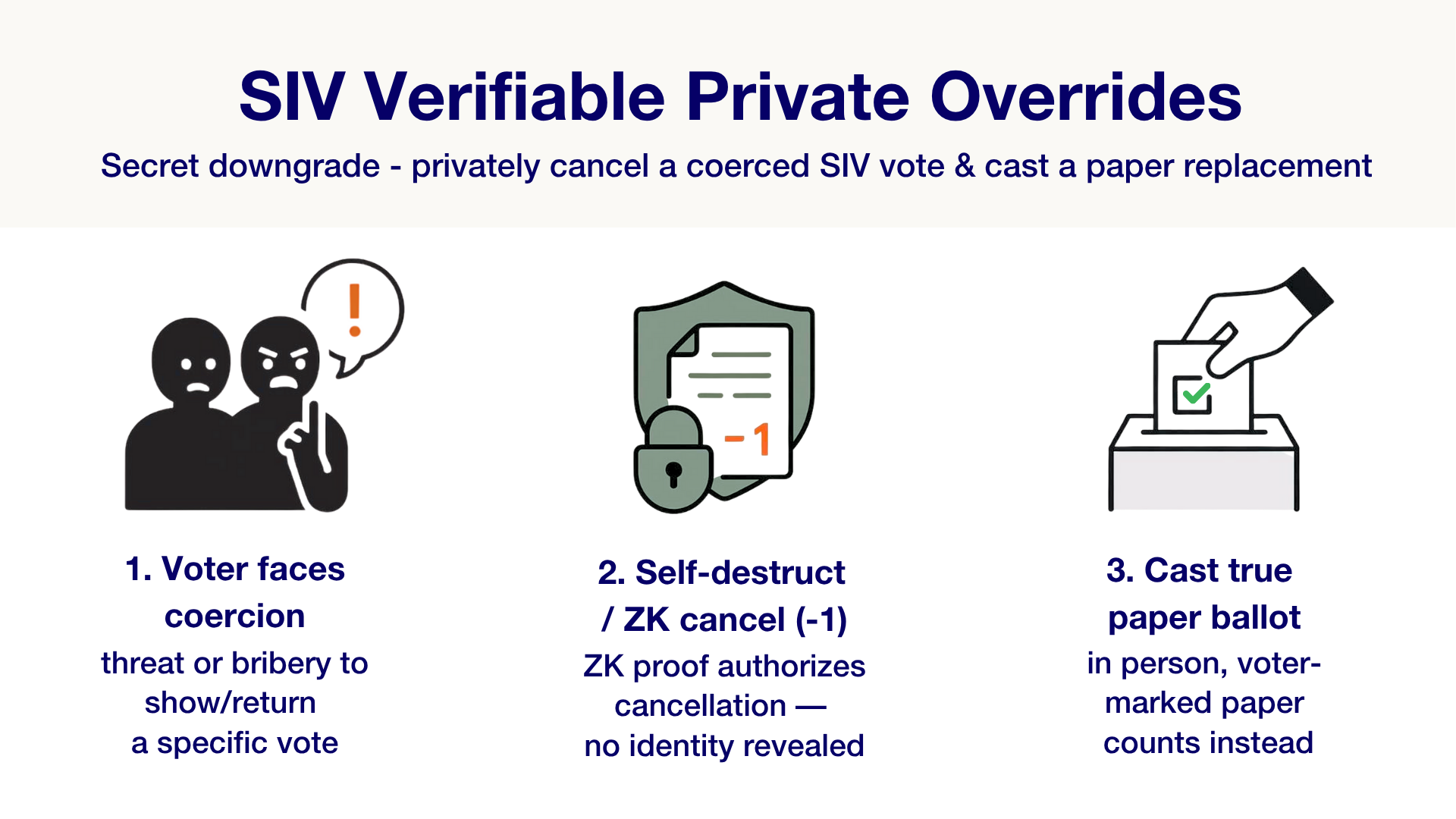
At a high level, the idea is simple but powerful:
If someone pressures you to vote a certain way — or offers you money for your vote — you can appear to comply, then privately & securely cancel your digital vote at a polling station, and submit a paper ballot reflecting your honest choices.
This solution matches the security level of traditional paper-based voting systems:
Although highly illegal, it is already physically possible with paper voting — especially vote-by-mail ballots — for someone to record & send a video voting a certain way to a third-party vote buyer. A slight reassurance is that such videos can be faked, using Hollywood magic or AI deepfake technology.
Unlike paper voting, SIV provides unforgeable proof of vote-cast-and-counted-as-intended. This verifiability is extremely valuable, as it enables SIV elections to be tamper-evident in the face of on-device malware and rogue server threats. But election security specialists have raised concerns that this unforgeable verifiability makes it too easy to prove to 3rd parties how one voted.
The new Verifiable Private Overrides capability is like a cryptographic analog to the deepfake video approach: it lets a voter show apparent proof to a buyer or coercer, while later being able to privately override their unfreely cast vote.
Although the underlying ideas use advanced math — which can be verified publicly — using this new capability is designed to be easy & approachable for all voters. With election administrators' help, we expect the process to take voters no more than a few minutes.
Importantly, SIV's Overrides strongly protects against these 3 key threats:
- Third-party coercers or buyers can't tell whether their demanded vote was ultimately counted.
- Election administrators can’t abuse this power, to secretly suppress votes or change tallies.
- Malware on voters' devices can’t abuse this power, to secretly suppress votes or change tallies, by requiring Override authorization via a separate channel (e.g in person, but can be adapted to digital only settings).
Inspirations
1) One example in the e-voting world is Estonia, which has offered digital voting in every government election since 2005. Specifically as a deterrent against vote selling, they have also long offered a similar “cast replacement override" option.
However, as we far as we can tell, their design appears to trade off vote-tally integrity, i.e. admins can secretly cheat. And introduced vulnerabilities to malware on voters’ own devices secretly stealing votes.
Our approach is inspired by theirs, but adds strong cryptographic guarantees against cheating, privacy-protecting auditability, and can't be used by on-device malware.
2) In the blockchain world, the well-known project MACI ("Minimal Anti-Collusion Infrastructure") was created to facilitate a similar "secret overrides" feature using Zero-Knowledge Proofs. This was noteworthy because the space is especially vulnerable to sophisticated vote-buying attacks. Specifically, many projects hold huge treasuries, with potentially billions of dollars of funds on the line, protected only by automated smart contract voting mechanisms. The space also has abundant pseudonymous actors, with access to "DeFi" loans, which make funding high-scale bribery attacks easy.
Inspired by their innovations, we've worked closely with their team to create SIV Verifiable Private Overrides, adapted for government election requirements. This includes strong defenses against on-device malware, high-scale throughput without gas fees or other network limitations, and easy usability.
Usability
For most voters, nothing changes. The “happy path” remains simple.
Some other coercion-resistant designs, like ThreeBallot, require all voters to use complex ballot structures, even if they aren’t under threat.
SIV’s approach keeps the system simple for the majority of voters — while still protecting the edge cases, and preserving long-term verifiability.
Learn more
We’ve recently gotten the core mechanism working — what started as a promising idea is now cryptographically functional.
We're excited to share more details about this system now that we've reached this milestone.
While we’re still preparing more extensive technical write-ups and documentation, you can already explore the existing working code and core technical specifications here: github.com/siv-org/verifiable-private-overrides